There are countless articles about the enormous financial and business impact of cyber-crimes, and while many organizations with fewer than 1,000 people view this as a big company problem, the reality is 46% of all cyber breaches impact organizations with fewer than 1,000 people and 61% of 2021 cyberattacks targeted these small and medium organizations (often called SMBs).
So, if this is such a big problem, why aren’t these SMBs doing more to protect themselves? Four things make a large part of this issue:
- It’s a foreign language. When people start talking about phishing, ransomware, network infrastructure, and devices, those are words some people have heard, but they aren’t part of their day-to-day language in running their business. This makes it hard to know where to start.
- No sense of urgency. It’s fine to say huge dollars and high per centages of impact, but when you don’t understand it, or how to talk about it, it can become a “not here” bogeyman sort of fear where it might keep you up at night, but there is nothing on your to do list today that will help you feel you have mitigated the risk in a quantifiable way.
- No one is responsible for it. If you are smaller, and you don’t speak the language, and you don’t have a way to quantify the risk to drive a sense of urgency, it’s pretty hard to assign it to anyone when budgets are already pretty tight.
- There really is no one size fits all solution, and custom can be expensive. It’s easy to spend a lot of money on cybersecurity, but the good consulting companies often don’t want to help with little organizations with small budgets, things become even harder when the company doesn’t their own IT person – it’s literally often a family member they see once a year at Thanksgiving.
With this mix of challenges, and with hackers getting more sophisticated every day – hacking SMBs starts to look like stealing candy from a baby.
So, what’s the solution? Naturally there is no “silver bullet” for this, but for this piece, we will focus on the first point above – that it’s a foreign language.
One of the leading organizations helping SMBs with cybersecurity today is the Cyber Readiness Institute, and if you go to their web site and see that they have a “starter kit” which looks like this:

This seems like a great starter kit – but if point #1 above is true, then starting with cyber-lingo is going to keep some companies stuck at #1 and never get to 2-4, which would result in them understanding their risks and knowing what resources are needed to mitigate them today, and as their business evolves going forward.
My suggestion for getting past #1, is to start with words the business uses every day and use that to connect to the language like that in the starter kit above. Once you have bridged #1, then the path and priority for 2-4 become clearer. What do I mean by this, well there are many kinds of organizations, from non-profits, to retail, to professional services (doctors, lawyers, consultants, etc.) and they each talk about things a little differently. What if you start with the basic digital assets of a type of organization, such as a professional services firm, and categorized which would have the highest risk, pain, or cost, if they were in the hands of a hacker. See the below example which is purely illustrative and not based on actual risk of loss/hack data::
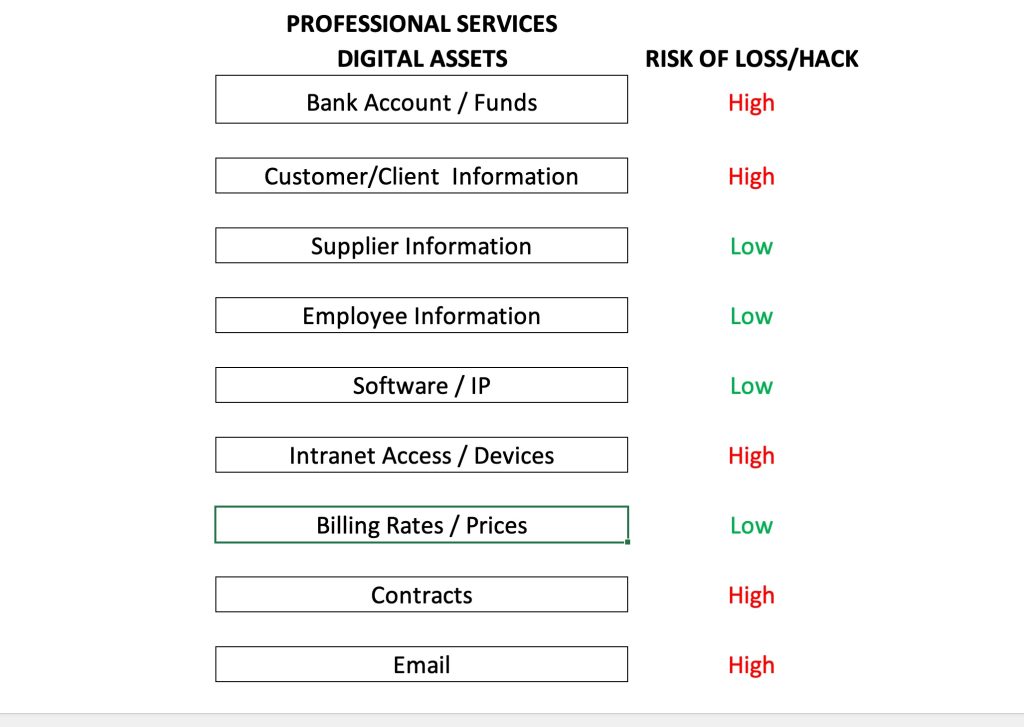
Note – this is fictional data in terms of the risk column, but I think this would be a clear way for a leader in a professional services organization to start the discussion. With this foundation, you can start to discuss all of the things in the starter kit and help the business get on their way.
Not to suggest this is perfect, only making the simple point that if you start by talking about something this organization is already talking about – and then link it to something else, be it cybersecurity, cloud services, or what have you – it seems like that would significantly increase the odds of helping that organization understand where they are, what they need, and what a roadmap might look like for them in terms of costs, risks, and other tradeoffs.
We’d love to get your thoughts on this. The next posts will dig further into bullets 2-4 above.
Leave a Reply